The development of digital technology has greatly enhanced convenience in our daily lives. However, as a side effect, the threat of the cyber environment has become increasingly sophisticated and advanced. The Information Security Center at NC has concluded that, in order to respond to the constantly evolving security threats, we need to move beyond simply preparing the best solutions and shift our perception of security itself. NC implemented the zero-trust model in 2019 to reinforce the company’s security system. The zero-trust model is a security paradigm that follows the principle of “not trusting anything until verified.” “Technology: Push the Boundaries” Series Episode 5 will showcase the journey of the Information Security Center as they incorporate the zero-trust model.
New Craving: In the Era of Digital Transformation, What Security Paradigm is Needed?
Improving Network Separation for Smooth Collaboration
Until 2019, NC divided its networks for development and internet use and protected data through a network separation environment that utilized a stand-alone development network for each game IP. However, a separated network environment with different email domains and difficulty transferring data between networks has made it challenging to collaborate effectively with other organizations. Furthermore, the developers had to install PCs throughout the network, which resulted in significant expenses for asset purchases and limitations in implementing new technologies such as cloud computing.
Due to these downsides, there were constant internal discussions about the need to integrate the networks. However, there was a concern that network integration could increase security risks more than the separated network environment. The first task that the Information Security Center faced was to integrate the network and enhance the security level.
Arising Security Threats from Technology Development
With the development of cloud computing and mobile technology, the boundaries of network are falling apart at a fast pace. In the past, company assets were only accessible within the physical realm of the company. However, now all employees can access data and infrastructure from anywhere outside the company. This phenomenon has accelerated since the COVID-19 pandemic. This means that there are more routes for hackers to exploit, and that the number of variables that need to be controlled increases from a company security perspective. The Information Security Center had to develop countermeasures to address the security risks that arise from rapidly changing technologies and social environments.
Never-Ending Challenge: Building a Trustworthy Security System through Zero Trust
Assigning Minimal Service Access Permissions by Verifying User and Device Security Levels
In 2019, to address this task, the Information Security Center implemented the zero-trust model, which is the latest global security trend. In the previous security model, anyone who successfully entered the intranet was granted all authority. As a result, hackers often targeted employee IDs and passwords.
By contrast, the zero-trust model assigns trust levels based on the condition of the device, user, or service, rather than the network boundary. All user activities are monitored in real-time, and if unusual activity is detected, the security officer can take immediate measures.
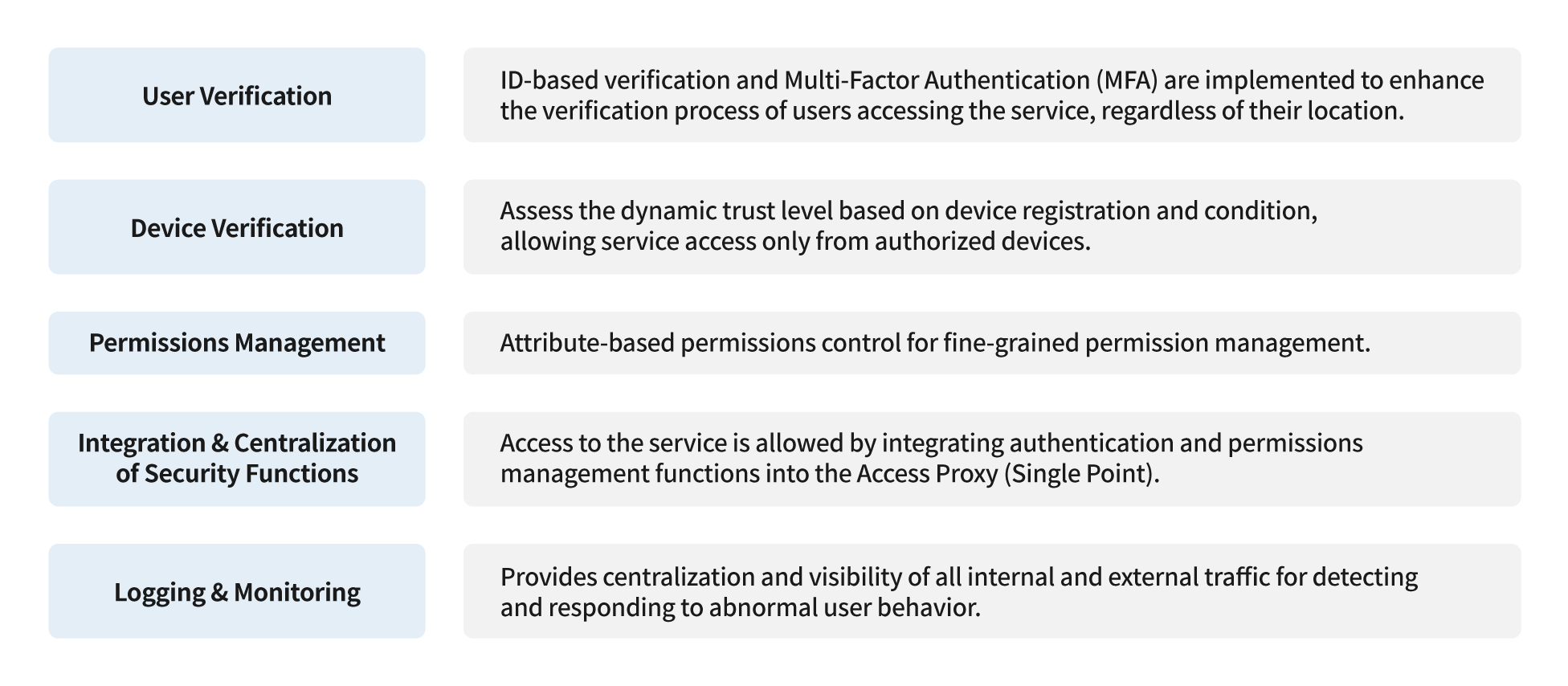

The Information Security Center summarized the seven principles of zero-trust realization suggested in NIST’s “SP 800-207” report into five.
The National Institute of Standards and Technology (NIST) suggested seven principles that serve as guidelines in realizing the zero-trust model in the “SP 800-207” report. The Information Security Center summarized them into five. The most important ones were user verification, device verification, and permissions management. The core of the zero-trust model is to verify the security level of users and their devices and grant permission to access individual services differently based on the security level. The Information Security Center developed NC’s own zero-trust architecture based on the principles in the “SP 800-207” report and implemented it step by step.
Stage 1. Developing NC’s Own Zero-Trust Architecture
First, the Information Security Center interviewed various departments within the company and defined four major scenarios in the work environment that would require the implementation of the zero-trust model at NC. In each scenario, the Information Security Center identified the types of technical elements that must be supported and the potential results that can be achieved.
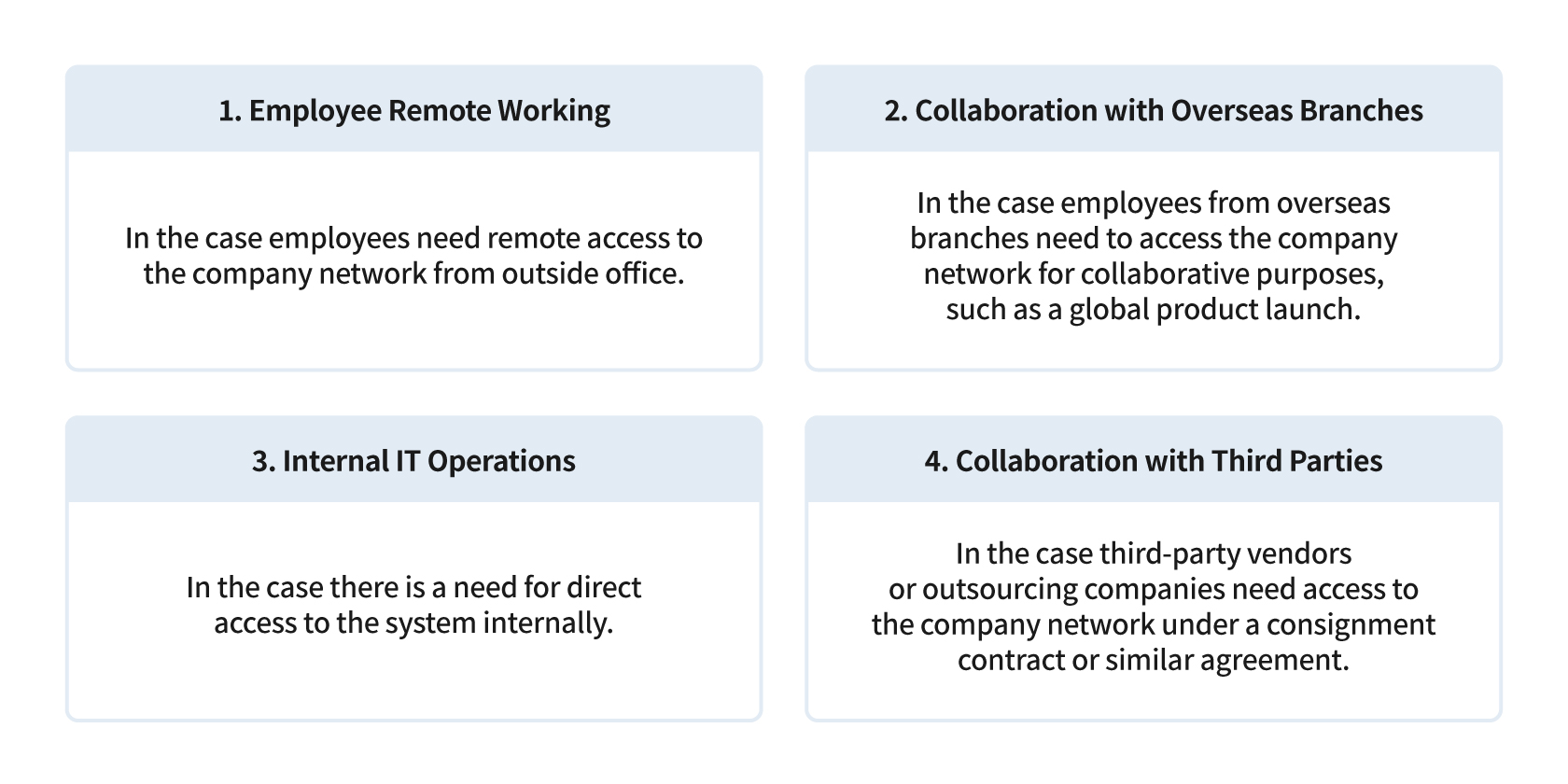

4 Scenarios Defining the Work Environment Requiring the Implementation of a Zero-Trust Model at NC
For the next step, the Information Security Center built NC’s own security architecture (zero-trust architecture) associated with the four defined scenarios and the implementation principles of the zero-trust model. Security architecture needs a technological solution that goes beyond theory; the Information Security Center developed a security architecture that suits NC’s work environment, based on Microsoft’s zero-trust model.
First, regarding devices, the Information Security Center made it mandatory to install a security control agent on mobile devices such as laptops and smartphones. This is a feature that allows the user to connect to the intranet by taking into account various factors, such as whether the device is a company-registered device, whether vaccines and other data leak prevention solutions are installed, and whether the security patch is the latest version.
The system allows access by checking the real-time trust level of factors such as geographic location and access permissions for users. Additionally, a two-step verification system was established, which includes OTP and biometric verification methods that go beyond the one-step verification based on IDs and passwords.
Lastly, the system was designed to control access to the service based on the real-time status of the device and user, or enable security measures such as blocking downloads. A monitoring system was also built to continuously assess the risk level concerning abnormal user behaviors.
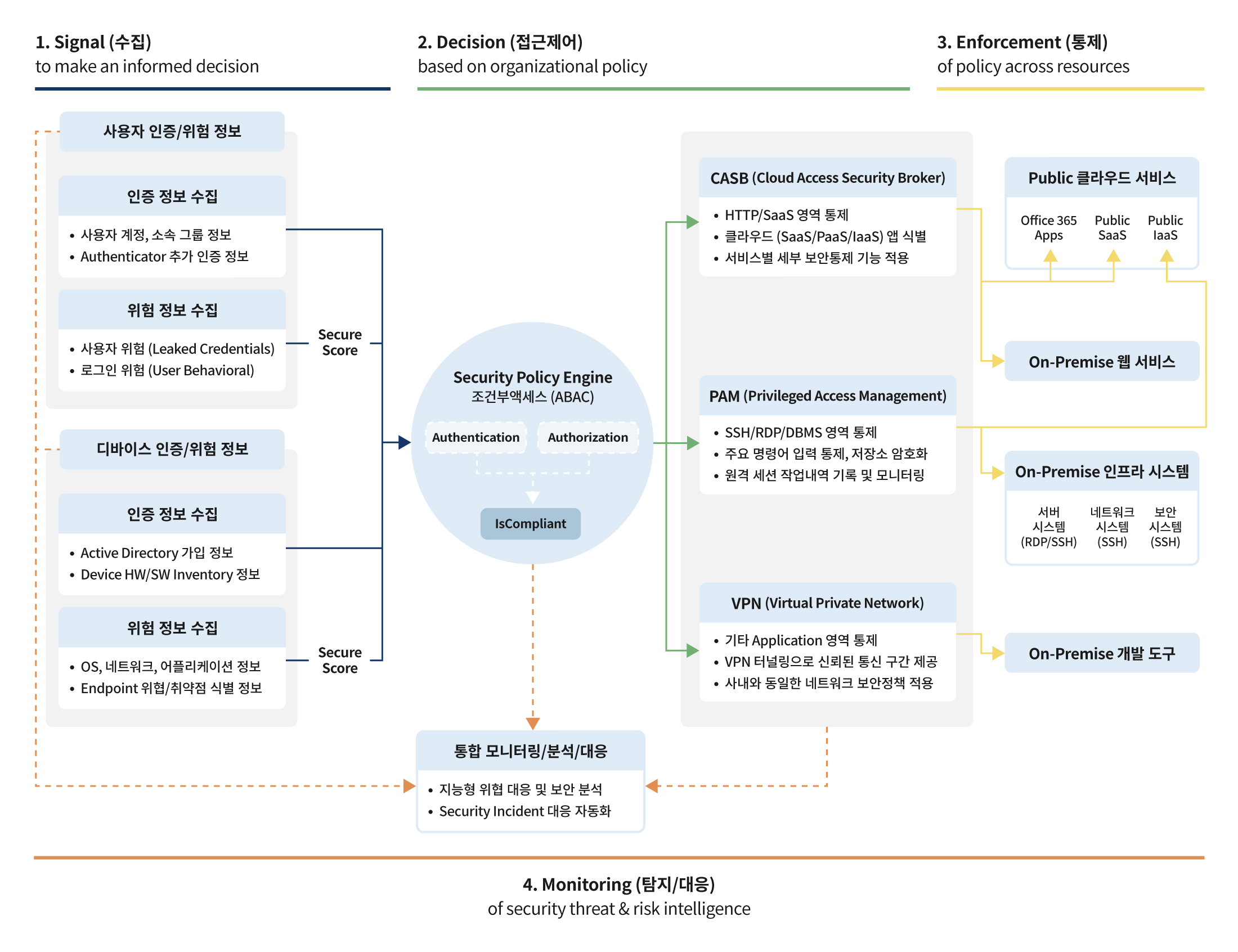

NC’s Zero-Trust Architecture (ZTA) Defined by the Information Security Center. It collects information about users and devices and assigns scores, which serve as the basis for managing and controlling access permissions. When it detects an unusual pattern while monitoring all user behaviors, it can respond swiftly.
Stage 2. Building a Security Environment for Global Leap
While the Information Security Center implemented the zero-trust model to build up a security system, the needs for a new security environment continued to arise. With the launch of Lineage W in 2021 and the increasing collaborations with global partners such as overseas branches and third-party vendors, on-site departments saw a surge in the need to use *SaaS-based external services as collaboration tools. The Information Security Center defined the implementation process of the zero-trust model from 2019 to 2021 as Stage 1. To address the unresolved tasks from Stage 1, the center began its second journey (Stage 2) in 2022.
*SaaS: An acronym for “Software as a Service,” it refers to the method of suppliers providing software, such as Microsoft Office 365, Slack, or Figma, via cloud computing. Users access such software through cloud services.
There are three major goals for Stage 2. The first goal is to develop a security architecture that satisfies all the principles of the zero-trust model. The Information Security Center succeeded in implementing many principles in Stage 1, but there were issues that were not addressed, specifically related to controlling access permissions for connecting to various internal and external services based on the security levels of the users and their devices. The Information Security Center has determined that there is currently “no single solution” that fully satisfies all principles, and as such, is adopting a variety of related solutions in combination to seek out solutions. At the same time, the center aims to increase the security maturity of the core elements that were implemented during Stage 1.
The second goal involves establishing a detailed classification system for services and data based on specific grades. Currently, NC protects all data and services using a single security grade. This is inefficient from both a resource management and collaboration perspective. The Information Security Center plans to classify all internal data and services into four grades and apply differentiated security policies for each grade. When this task is completed, high-security grade data and services will have improved security levels, and a more flexible environment will be provided for relatively low-security grade data and services.
The final goal is to establish User Behavior Analytics (UBA), which analyzes user behaviors. Compared to general monitoring for unusual behaviors, the zero-trust model collects a significantly larger amount and wider range of data since it monitors all user behaviors. If a UBA system is constructed to analyze bulk user behavior data, it enables more sophisticated analysis when monitoring for information leakage and allows real-time blocking of access permissions when detecting abnormal user patterns.
Next Change: There is No End in Security
The rapid implementation of the zero-trust model has yielded positive results for NC. The company was able to handle remote work flexibly in response to the COVID-19 pandemic and improved employee convenience by safely integrating separated networks. As a result of these achievements, NC was ranked as a top 1% global company in the information security and privacy protection sectors by ESG Risk Ratings last year.
However, NC’s zero-trust model is an ongoing journey. Realizing a technical solution is not the end goal of the zero-trust model. A detailed understanding of security-related elements, such as the company’s services, data, devices, and users, is required, and a closely integrated management system must be established across the entire organization. The Information Security Center plans to implement these processes throughout all areas of the organization, identify any potential blind spots in security, and continuously address them to ensure the highest level of security. The challenge and efforts to build a trustworthy security system will continue.
 Facebook
Facebook  Twitter
Twitter  Reddit
Reddit  LinkedIn
LinkedIn  Email
Email  Copy URL
Copy URL 






